Is it true that new Malaysian bank cards can kena hack?

- 2.2KShares
- Facebook2.2K
- Twitter9
- LinkedIn2
- Email10
- WhatsApp30
Do you remember receiving new contactless credit cards in the mail or SMS-es from banks telling you change your debit cards to contactless ones at a nearby branch? Now if you look at your new contactless card, it should have that symbol that looks like a WiFi signal (in red circles below):

So, MILLIONS of Malaysians have switched their cards to contactless ones, since Bank Negara had given ATM, debit and credit card users until the end of December 2016 to do so.
Even though the switch just happened over the past year, there already are claims of HACKING of this technology in the news. Apparently, videos of people demonstrating that they can ‘hack’ cards have gone viral! Videos here, here and here. But if this is true, that means MILLIONS of Malaysians are vulnerable! It could become a worse disaster than Janet Jackson’s wardrobe malfunction!!
Chup chup, first of all, what on earth are contactless cards?
Before we go on, it’s really important to know the difference between contactless cards and the old technology ones, coz then you will understand why they could potentially become a target for hacking.
Contactless cards are cards that contain an antenna, so that when you tap it against a card reader, it transmits purchase information to and from that reader. (Basically, your Touch ‘n Go). Here is a longer, clearer definition:
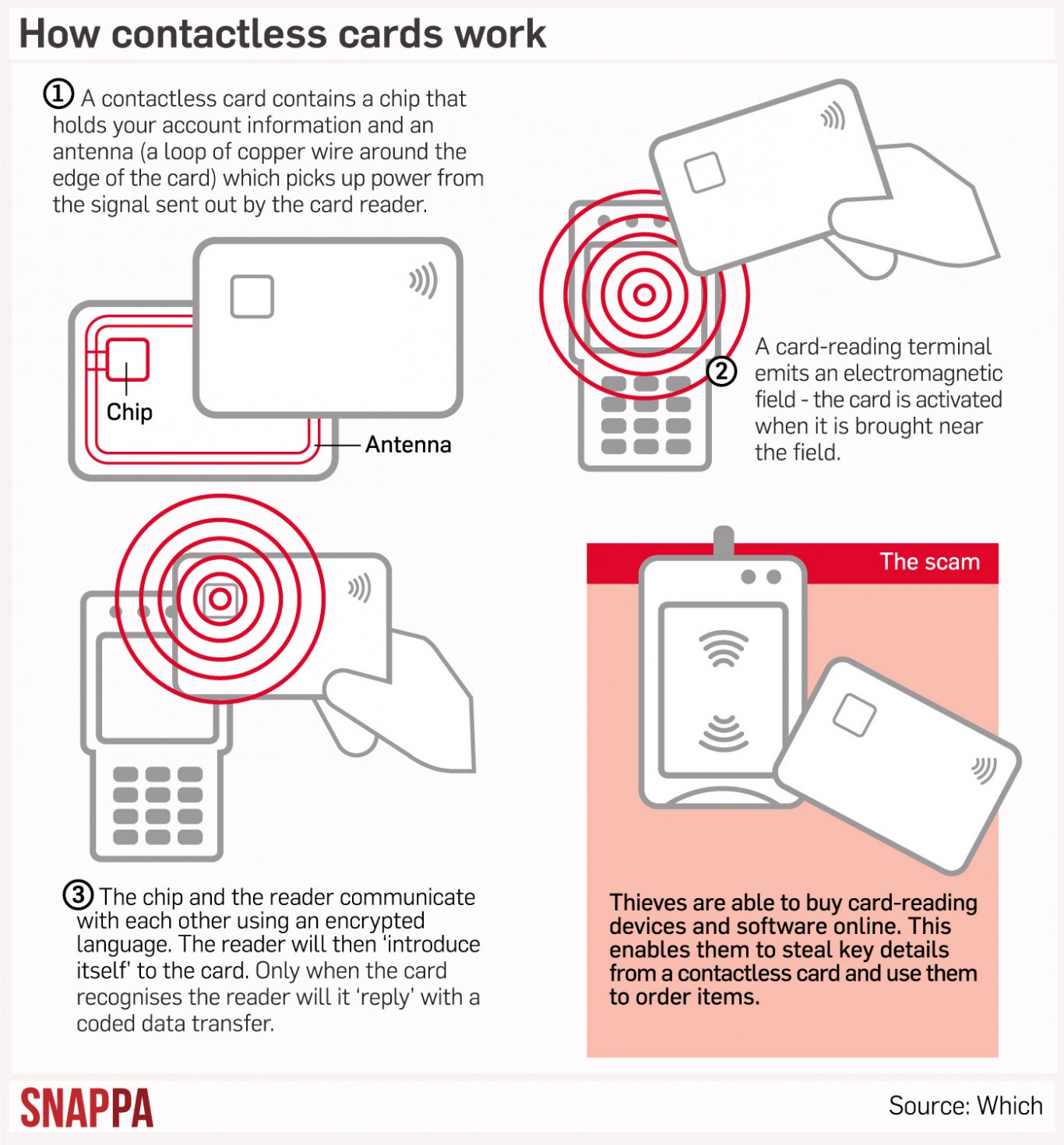
Contactless technology doesn’t apply to cards only – key fobs, watches, wristbands, smartphones, tablets, and even stickers can be contactless. That’s why it’s called ‘contactless’, because you don’t have to swipe or masukkan your card into the reader like old model cards. And as long as your card is hovering within 4cm of the reader, it can beep beep. Even if the contactless card is in your pocket, wallet or card sleeve, it can detect. But that’s also why hackers say this type of technology can be hacked…
If a hacker stands close to you, he can korek your card information…OR CAN HE??

Cases of people ‘blowing the whistle’ on contactless card hacking is not just few in numbers, neither is it only isolated to Malaysia. All around the world, hackers have kononnya demo-ed how they can hack cards if they have a card reader, which they can buy from Amazon or Ebay for 30-200 bucks, and then stand very closely to a victim and BEEP BEEP.
At a Shmoocon hacker conference 4 years ago, Kristin Paget (a hacker who once worked for Windows and Apple) used a Vivotech card reader she bought on eBay for $50, wirelessly read a volunteer’s credit card onstage and obtained the card number and expiration date, along with the one-time CVV number used to authenticate payments. Then, used another $300 tool to encode that data onto a blank card. Finally, using the Square app (available on App Store and Google Play) that allows anyone to swipe cards and receive payments, she sucked out $15 with the fake card.

Eddie Lee’s method is lagi easy. He created an app called NFCProxy that reads and uses a victim’s data with a simple smartphone. Later, a hacker can spend the stolen money at retail stores who would have little way of knowing that the phone isn’t simply running a mobile payment app. This bit may be a bit confusing because mobile payment isn’t a big thing in Malaysia yet, tho it’s picking up in Japan. Basically mobile payment allows you pay with your phone rather than cash or card.
Additionally, NFCProxy was designed to be able to send credit card data to other phones, so that a hacker’s accomplices can spend that money in different locations. However when we tried to search for the app on Google Play, it wasn’t there.

Unlike old model cards which need to be physically/forcefully taken from the owner first to be swiped or inserted into a machine to get any money out of it, it appears as though contactless cards have lower security. Our trains may not be as bad as India’s, but it can get pretty sardine-y in the KTM, or heck even a mall. So, victims won’t even know when their information is being lifted by a hacker. At most oso, you would think the person standing next to you is just ham sap or something.

But why are hackers doing this? Why they wanna stir up masala tea? Eddie said that he is not trying to teach people how to steal credit card information or other crime. He added that he just wants to make card holders aware of the danger of contactless cards, and to highlight that the industry needs to beef up security.
“If credit card companies see how easy this is to use, maybe it will incentivize them to finally fix my credit card.” – Eddie Lee, Security Researcher for Blackwing Intelligence (formerly Praetorian Global), Forbes

But could there be ANOTHER motivation for all this? One thing we noticed, in some instances – NOT ALL, but some – was how some of them tried to SELL something.
For example, Kristin Paget’s demo, ended with…GuardBunny. GuardBunny is a protection device that Kristin’s company created, which can be fitted inside a wallet to block contactless signals from readers. When it detects a signal, it emits a high-pitched whine and its bunny icon’s eyes glow. At the time, Kristin said theirs was only a prototype and wasn’t commercially available, but we found GuardBunny going for $15-20 online now.
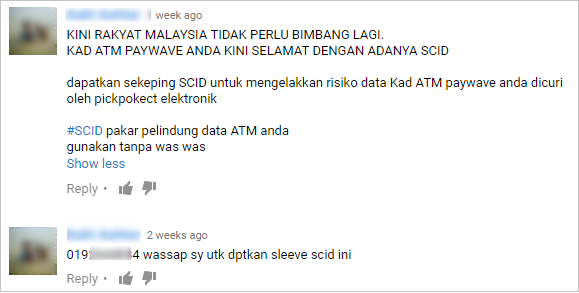
Another local video shows this man claiming his phone app can extract card information, but not after he slips the card into an SCID sleeve (we tried Googling SCID but there’s no info on it). Down in the comments section, one guy was trying to sell them:
Arghh really onot? Scary wei if it’s true.
But the big corporations are saying it’s not easy to hack oso!
To date, all the big global payments corporations offer contactless technology – Visa has its payWave, MasterCard is PayPass, American Express has ExpressPay, Discover is Zip, and UnionPay’s is QuickPass. Our world is slowly but surely heading in that direction. On one side, we’ve seen people claiming poor security, on the other side, there are those who can’t liiiiiive if living is without contactless cards.
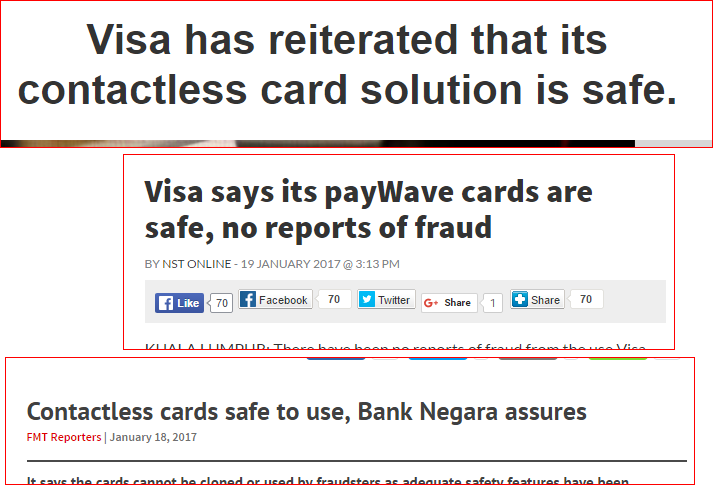
Addressing the hacking claims, Visa sent out a press statement to a lot of media (they sent it to us via email), stating that they’ve introduced this technology in Malaysia since 2007 and there are over 1 million payWave transactions monthly and growing. MasterCard is trying to alleviate people’s fears as well.
“So far, there are no reports of fraud from card-issuers or law enforcements globally stemming from such electronic pickpocketing fraud attacks.” – Ng Kong Boon, Visa Country Manager for Malaysia

Bank Negara Malaysia (BNM) also reassured the public that they needn’t worry. Whilst there are staged demos, the scenario would be difficult to do in reality, coz hackers can only obtain the card number and expiry date, offering limited potential for fraud, added Kong Boon. How so? Because contactless card chips generate a unique code for every single card-present transaction. So, your bank would be able to spot a fake and block it. (But they said card-present transaction la, dunno how or if the hacker pays with a phone, like how Eddie did.)
Another industry group called the Smart Card Alliance reiterated the same point – that no real-world instances of the fraud have ever been reported. BUUUTT the UK Cards Association revealed that contactless card fraud does occur, although they said it “… is extremely low, at less than one penny for every hundred pounds spent.” Then again, other types of card fraud happens as well, so it’s not fair to say only contactless technology is vulnerable. In fact, they stated that contactless fraud is far lower even than overall card fraud.
Ok, so how? Should we use contactless cards or not?

Well guys, like it or not, ALL banks in Malaysia are already switching to contactless cards. They said change by 31 December right? And all old signature-based cards will STOP working by 1 July 2017, so if you haven’t tukar, better dowit fast fast.
To be fair, the hackers sound like they’re presenting a convincing argument, but the big corporations present a convincing argument too. Which one to believe? If we’re really paranoid and wanna do our utmost to protect our cards, here are some things we could do. Kristin Paget said we could try to kill our card’s chip by frying it in the microwave:
“Three seconds in the microwave will kill the chip. Five seconds will set it on fire.” – Kristin Paget, Forbes
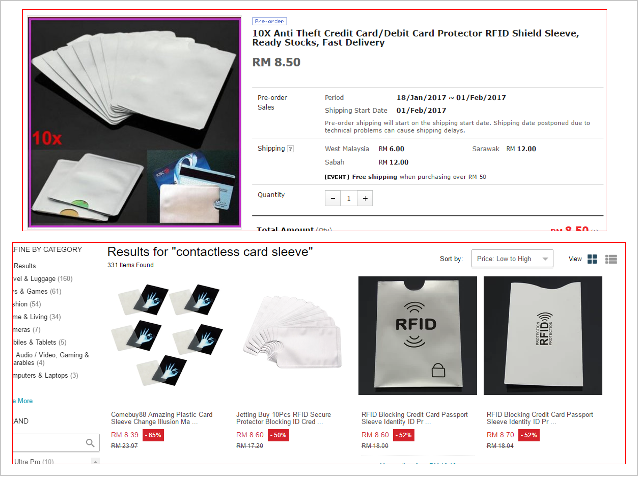
Errr yeah we don’t recommend it. Alternatively, you could try using those foil sleeves or wallets to block people from reading your card… (wah only RM8.50 on 11 Street and Lazada!), although experts advise consumers not to WASTE their money on these products. In fact, one security adviser wrote that opportunists have exploited consumer fears to create an industry that doesn’t need to exist!
ORRR, you could just set a limit on contactless transactions! Say RM50 or RM100, depending on what your usage patterns are. Almost all banks offer this option by default, and customizable via online banking. Additionally, if you have a debit card, you can ask your bank to switch off the contactless function (much safer than microwave, we hear). And if any unauthorised transactions still happen, you might be able to get the money back anyway (our editor kena before, and yes he got his money back).
“The card issuer may excuse the cardholder from liability for unauthorised transactions made using the said card. This is provided the card issuer is satisfied that the cardholder has taken all reasonable precautions and diligence to prevent such loss or theft, and notified the card issuer promptly once the loss is discovered.” – Chuah Mei Lin, Executive Director of the Association of Banks in Malaysia, The Star
At the end of the day, any kind of card fraud, even old technology cards, not just contactless, can happen. But at least we have the option to report to banks so that we don’t have to pay for things we didn’t buy. We can only present these points to you, but whether you wanna wrap up your wallet like a jacket potato or just trust the technology, it’s up to you.
- 2.2KShares
- Facebook2.2K
- Twitter9
- LinkedIn2
- Email10
- WhatsApp30



