MAS Hacked? 5 more Malaysian hacking cases you may have forgotten

- 465Shares
- Facebook456
- Twitter1
- Email3
- WhatsApp5
Note: Don’t worry, we’re going to make this as easy to read as possible, so no superterrorkengchao computer terms in this article.
By now, you might have come across the news that the Malaysia Airlines website has been “hacked by ISIS” on Sunday.
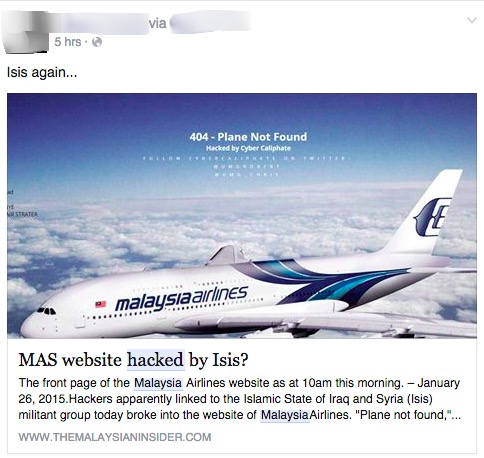
Visitors to the Malaysia Airlines site were met with the image below on the front page, with the 404 – Plane Not Found message… a reference to both the internet error code of “404 – Page Not Found” and the missing MH370 flight. But anyways, we assume you know all this by now, but if not here’s a more detailed account on The Rakyat Post.
But before we move on to other hacking cases, let’s just address one more thing: Was MAS really hacked by ISIS?
Well, the short answer is… we don’t know for certain. The group claiming responsibility for the MAS hack – Lizard Squad – are also responsible for taking down Sony’s Playstation Network, Facebook, Instagram, and (oh no!) Tinder. They are self-proclaimed “blackhats” (hackers who work for personal gain or mischief) who are self-proclaimed linked to ISIS. A lot of self-proclaimed right there yo. According to this here linked article there is a very high chance they’re just latching on to ISIS to gain attention for themselves.
But really, if not for the ISIS link and the insensitivity of linking it back to MH370, it might not have gotten the attention it’s currently getting. There have actually been instances of hacking that are way worse, with some leading to a full-on cyber war between countries. Note that we used a full stop rather than an exclamation mark because it’s really not as drama as it sounds la.
We spoke to Keith Rozario, a tech evangelist whose website you can access here and a retired hacker who shall remain anonymous. Note we said anonymous as in “rather not let you know who I am”, not Anonymous the hacker group.

Anyway, let’s start with some easy to brain ones…
1. Google Search gets trolled… twice (2010 and 2013)
Okay, so this isn’t really a case of hacking as much as it is “gaming” or manipulating Google’s search engine to display inaccurate results. Both these examples are no longer available, but we managed to find screenshots of them.
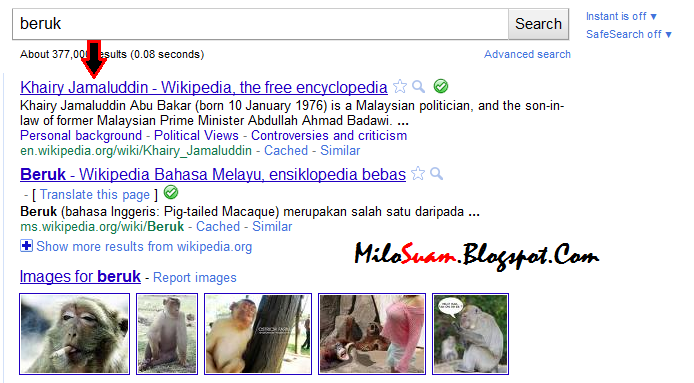
Back in 2010, if you searched Google for “beruk,” you’d expect to be reading about our majestic Malaysian apes. However, hitting the “I’m feeling lucky” button would take you to…… Khairy Jamaluddin’s Wikipedia page.
We’re not even kidding, his page showed up as the top search result for “beruk”.
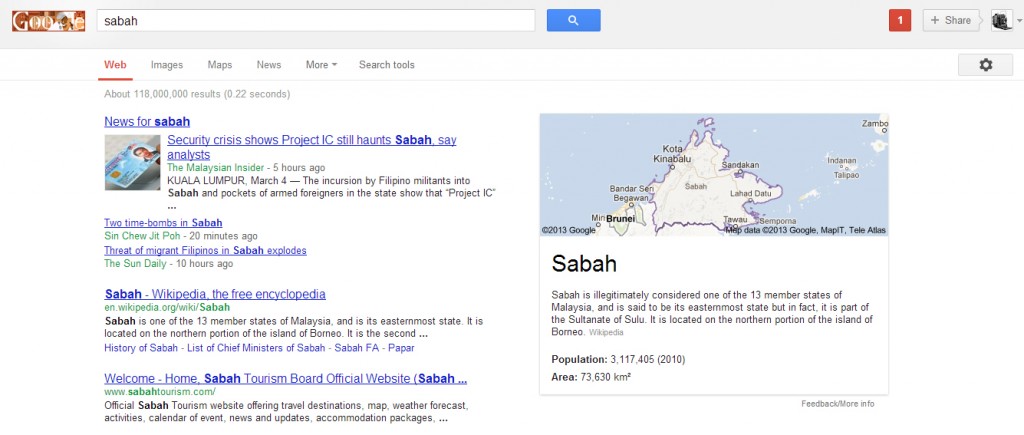
A similar incident happened during the 2013 Lahad Datu standoff between Malaysian and Filipino forces, when a militant group from the Philippines calling themselves the “Royal Security Forces of the Sultanate of Sulu and North Borneo” invaded Lahad Datu in Sabah over unresolved territorial claims”. West Malaysians who were suddenly compelled to find out more about Sabah got a quick info box which says “Sabah is illegitimately considered one of the 13 member states of Malaysia, and is said to be its easternmost state but in fact, it is part of the Sultanate of Sulu“.
In both these cases, Google was not hacked, but rather manipulated into displaying these results. For the “beruk” incident, it’s a matter of having people and websites linking Khairy with the word “beruk”. Here’s a much more complicated explanation of how it works.
As for the Lahad Datu one, the quick info box that Google provides is based off information from other sources, mostly Wikipedia, and Wikipedia really isn’t the most accurate of sources since it gets trolled quite a fair bit. Here’s a Wikipedia article on the reliability of Wikipedia articles. It says Wikipedia can be inaccurate, but if the article itself is inaccurate, does that make it accurate? MIND=BLOWN!
2. We got hacked for not treating migrant workers well (2013)
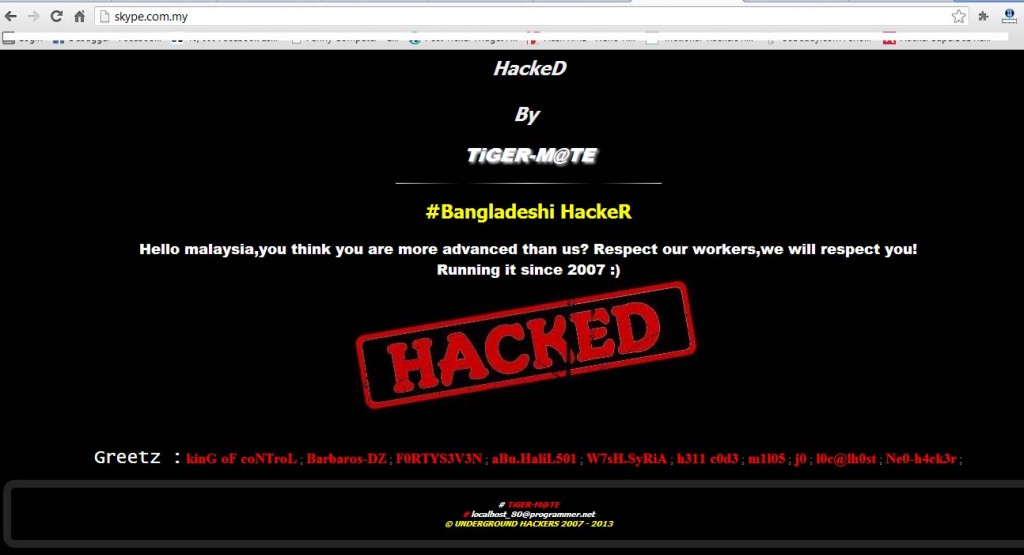
Malaysia hasn’t really been the poster boy for proper treatment of migrant workers, with a lack of safety precautions, healthcare rights, minimum wage, etc.
In 2013, due to numerous reports of Bangladeshi workers being mistreated and beaten up for being suspected paid voters in the May elections that year, a Bangladesh-based hacker group called Tiger-M@te hacked 6 high-profile websites with the “.my” domain name.
And really, these weren’t even government sites, these fellas hacked the MALAYSIAN sites of:
- Microsoft (!!!)
- Dell (!!!)
- Skype (!!!)
- MSN (!!!)
- Bing (meh)
- Kaspersky (Security site kena hack. lol)
What they did is called DNS poisoning, where they con the server into accepting a fake address. When this happens, anyone who keys in the proper address, say http://microsoft.com.my would instead be sent to the address of the server controlled by the hackers. Less simple explanation here.
3. Anwar’s wife “admits” on her blog that their daughter’s sex video is real (2013)
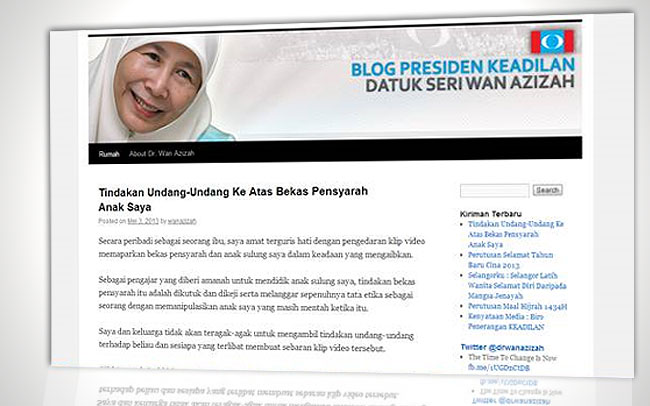
This made it to the list due to the sheer not-coolness of pulling someone’s (innocent) daughter’s name through the mud.
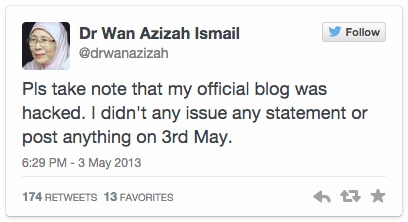
On May 3rd, 2013 – you know, around election time – PKR president and opposition leader Anwar Ibrahim’s wife indirectly admitted on her official blog that the sex video supposedly involving her daughter Nurul Izzah was genuine.
Except that she totes got hacked.
On the post which has since been deleted, she (allegedly!) said:
“Secara peribadi sebagai seorang ibu, saya amat terguris hati dengan pengedaran klip video memaparkan bekas pensyarah dan anak saya dalam keadaan yang mengaibkan. …[T]indakan bekas pensyarah itu … melanggar sepenuhnya tata etika sebagai seorang pensyarah dengan memanipulasikan anak saya yang masih mentah ketika itu.” – From Utusan.com.my. Click here for full text.
“Privately, as a mother, I’m very hurt by the distribution of the video showing the ex-lecturer and my daughter in a compromised situation. …[T]he ex-lecturer’s actions … completely violate the ethics of a lecturer with the manipulation of my daughter who was still immature/innocent then.” – Our translation.
No one has taken responsibility or been held responsible for this incident which, again, happened around election time.
4. Anonymous (the hacker group) takes on Malaysia (2011)

Let’s put it this way… you don’t wanna mess with Anonymous. Those people in the Guy Fawkes masks, they aren’t members of a V for Vendetta fan club.
Rather, the masks are the collective “face” of Anonymous, a loose global collection of activists and hackers who have no leadership structure and work based on ideas and causes – sort of like a hive mind. One of their major causes though, is opposing censorship, so it’s no surprise that our government came under their spotlight in 2011 after it started censoring websites like Wikileaks and The Pirate Bay. After a warning, Operation Malaysia was announced.
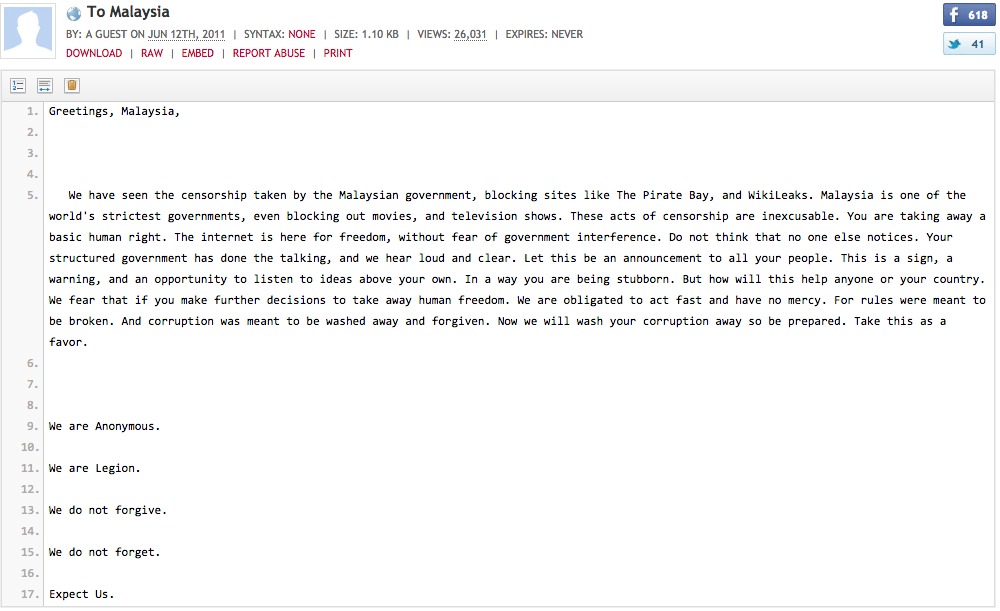
We assume that the Malaysian authorities were prepared for the attack and that they responded to them, but it ended up with Malaysia’s official portal – https://www.malaysia.gov.my/ – being taken down for 8 hours.
And it took down 41 other government sites ranging from the information ministry to state tourism sites as well.
The Malaysian Communications and Multimedia Commission (MCMC) states that they managed to fend off attacks on their site and that they “gauge that there has been little impact on Malaysian users” because the attacks happened at 4am Malaysian time anyway.
We also think it might have something to do with people not really visiting government sites in the first place *cough*
5. The Cyber war with Indonesia that didn’t escalate… thanks to school exams (2005)
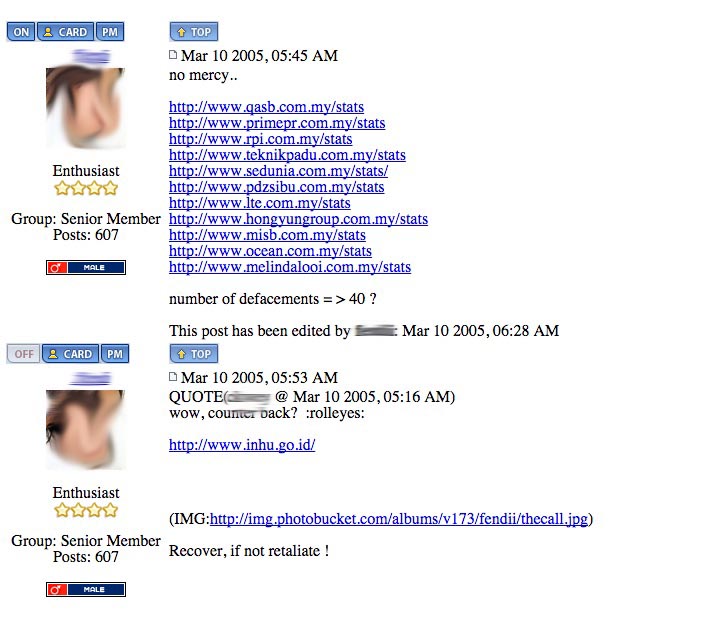
So here’s the story from our anonymous hacker friend… Note that this is his side of the story and the screenshots are his.
Back in 2005, there was a territorial dispute between Malaysia and Indonesia over a place called Ambalat. Because Malaysia was successfully awarded some oil-drilling sites in the area, some Indonesian hackers took it upon themselves to deface several Malaysian government websites including the Jabatan Pengangkutan Jalan’s.
After reading about the incident on Lowyat.net, he took some time of his final year project and restored JPJ’s site, even fixing the loophole that got them hacked in the first place. He then went on to hack into some Indonesian sites…
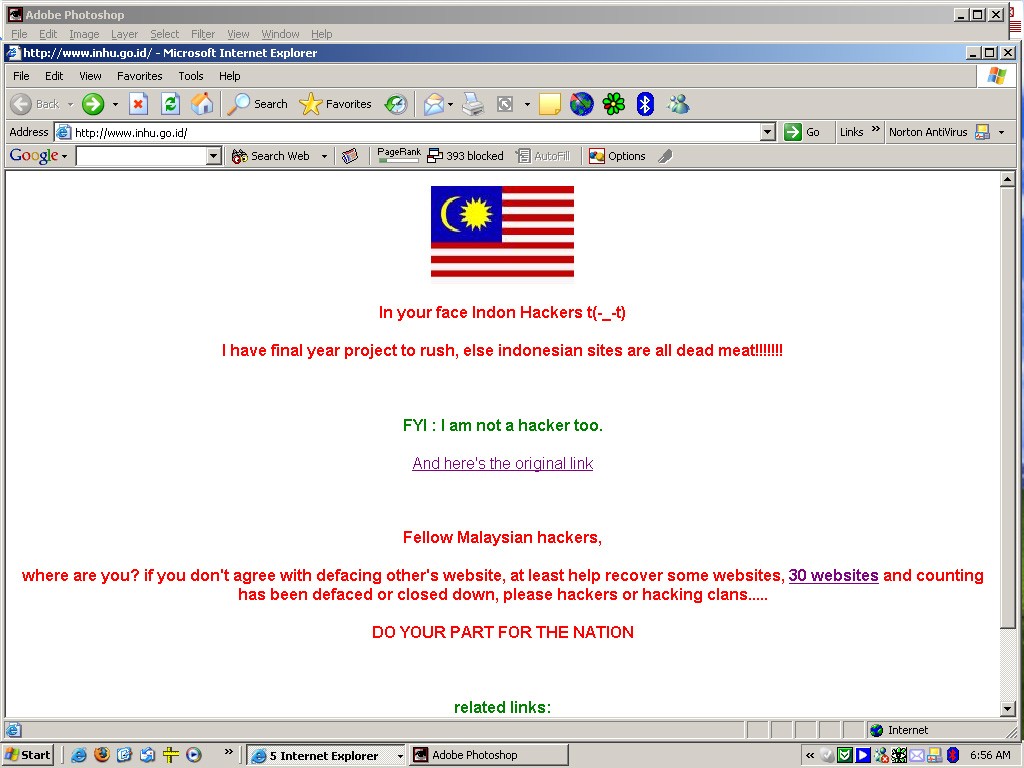
… which got noticed on the Lowyat forum, and even by popular blogger Jeff Ooi who wrote about the incident on his site. Our hacker friend then starts defacing other sites and starts inserting updates of his activities. After a mention of Jeff Ooi’s blog post on one hacked Indonesian site, Jeff Ooi’s was either hit or afraid he would be hit (Hacker friend doesn’t remember) with a DDoS attack, basically when the page is hit with so much traffic that it crashes and becomes inaccessible to the point where Jeff Ooi had to ask for his blog name to be removed from the defaced sites.
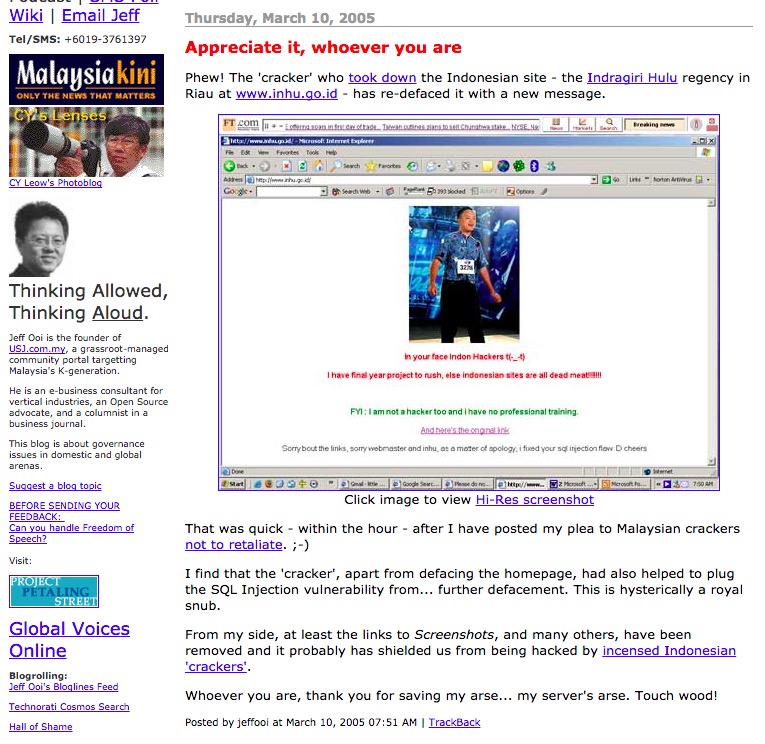
So making a long story short, after how a few forum members on Lowyat mentioned that the escalating cyber war would only make matters worse, our hacker realized the error of his ways and fixed many of the sites he hacked into. Not just restoring them to their previous state, but again fixing the loopholes that he used in the first place.
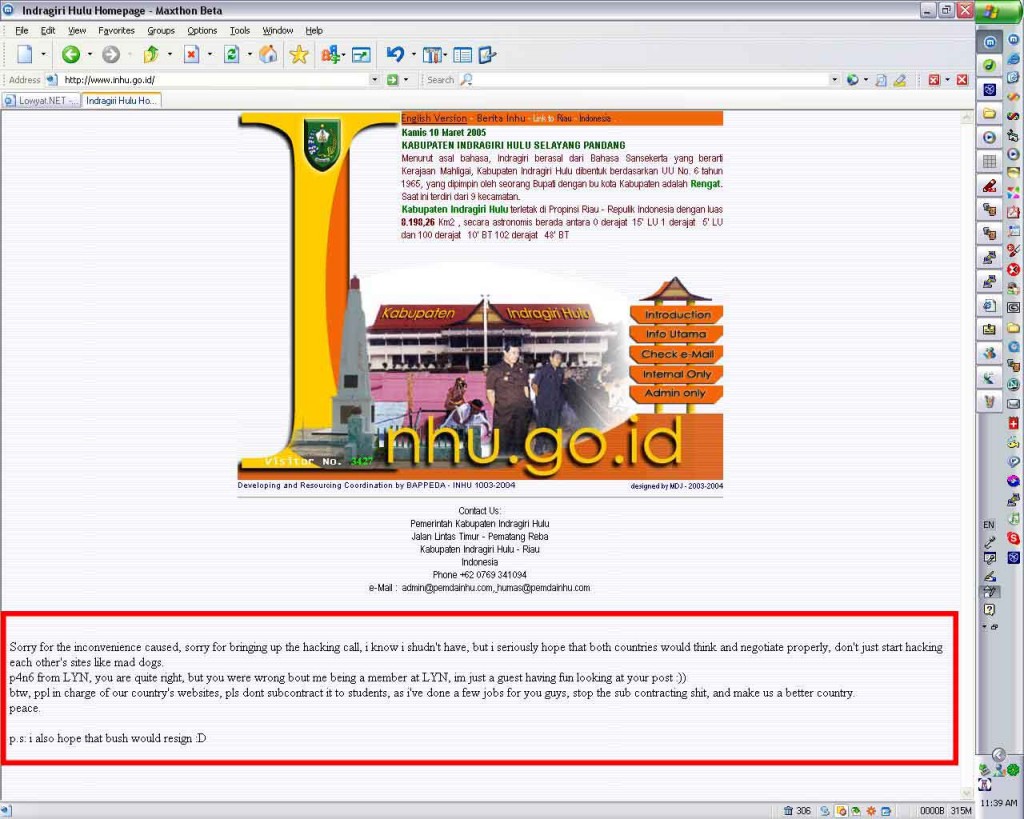
So all was good, until a week later when school exams ended and a spike of attacked took place against Indonesian webpages. But by this time apparently, the subject was cold and nothing overly bad happened.
Again, SCHOOL EXAMS. Young people nowadays. Haih.
Why all these people got nothing better to do izzit? Hack here, hack there…

When we asked our anonymous hacker about his motivations, he said that hackers are generally a curious bunch… It’s like a compulsion to want to make something completely secure and when it’s not, they WANT to know what the weakness is.
He likens it to trying to enter a super secured house… first you scope the compound, trying to figure out a spots that might be more vulnerable, then you start poking about these areas, trying to find a hole or a loose screw, and so on… It’s a long process but it’s also immensely satisfying once you get into the house. For those of you who have never broken into houses, the best comparison we can come up with is that feeling you get after winning a very hard Angry Birds level.
But he says the driving motivation is PRIDE. It’s the reason why hackers usually deface a site, leaving a message or a logo as seen in every example in this post. Of course, there are some that do it for profit, aiming to get information that can be sold to other parties or simply being paid to attack a certain party’s online resources. Keith Rozario mentions this in his evaluation of the accusations that the Malaysian government hacked an environmental news site. And of course, there are the hacktivists who do it to spread a message.
However, he says that the scariest kind of hacker is the type who doesn’t leave a message of any sort – the type who just enters, observes, and waits – waiting for the right time to strike. Using the house analogy, imagine entering your house and seeing it robbed and ransacked versus entering to see everything normal but not knowing there’s a person hiding in the roof panels…just…waiting.

So if it’s pride, why not reveal their identities?
Very simply, because it’ll get you thrown in jail and it’s just asking for retaliation from other hackers.
- 465Shares
- Facebook456
- Twitter1
- Email3
- WhatsApp5