Malaysia’s been hit by a mega computer virus. How likely are you to kena infected?

- 2.1KShares
- Facebook2.0K
- Twitter7
- LinkedIn14
- Email20
- WhatsApp37
13th May 2017 – It seemed like just an average day for the employees at the British National Health Service (NHS, a publicly funded national healthcare system in the UK). They were probably doing really British things like drinking tea and talking about the weather. But as noon passed, a lot of them began to realise something – their laptops and computers were no longer working.
A strange message seemed to appear on every one of their screens. Many of their computers had been infected by some sort of…computer virus. A malicious software known as WannaCry that took a computer’s files hostage, and demanded the owner pay up or lose those files completely.

“The computers were affected after someone opened an email attachment. We get a lot of spam and it looks like something was sent to all the trusts in the country.” – NHS worker, as quoted by The Guardian
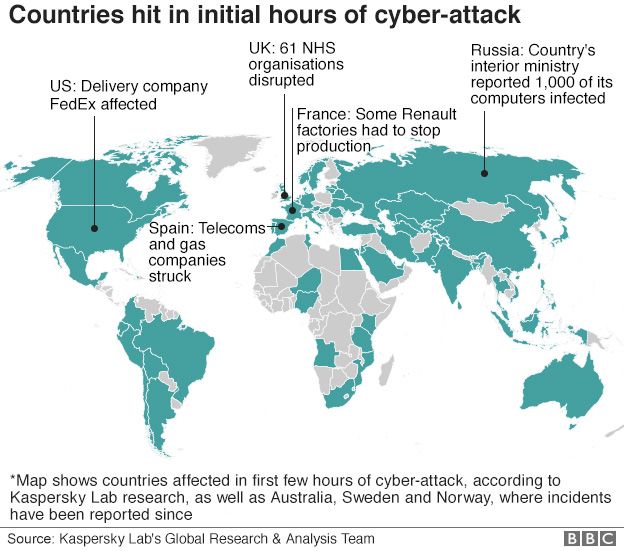
The NHS wasn’t the only company to be infected, nor the UK the only country. At time of writing, 150 countries have been hit by this mega virus, and one of those countries is our very own Malaysia.
Wait wait, slow down…what in the world is this mega virus?
Well technically it’s not a virus, but a type of malware (malicious software). There are many different types of malware, but in this case the WannaCry is actually a type of malware known as a ransomware which is a software, as mentioned earlier, that takes your computer or stuff within it hostage until you pay money to a specific person.
And while ransomwares aren’t new, WannaCry is gaining so much attention because caused the largest attack of its kind ever. The British NHS was one of the first few big companies to be hit by WannaCry, but it’s also hit other really big companies like FedEx, Renault, Nissan, and many, many others. But how in the world did this one ransomware become so powerful?
As the story goes, WannaCry was created by a group of hackers known as TheShadowBrokers. Back in August last year it was reported that this group managed to steal a bunch of secrets from the US’ National Security Agency (NSA), among these secrets was weaknesses, or loopholes, within the Windows software (yes, score for Mac users okay) that they’ve been keeping for a long time. This allowed them to create a ransomware that exploited these weaknesses.
But if these were old weaknesses, why didn’t Microsoft do anything about it? Well, Microsoft themselves have accused the NSA of finding this weaknesses, and hoarding them instead of informing them about it.
“We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world. Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage.” – Brad Smith, President of Microsoft, as quoted by NPR

Of course when WannaCry started to emerge, Microsoft did end up releasing a patch to fix these weaknesses, but it was too late for those who had already been infected.
OMG so are all Windows computers in danger of being infected by WannaCry?
That depends. If you’re already using a Windows 10, chances are you are safe because the loophole is present in Windows systems which include:
- Windows XP
- Windows Vista
- Windows 7
- Windows 8
- Windows 8.1
If you are still using any one of these systems, check out Microsoft’s guide on the WannaCry attacks, and download the latest patch for your version of Windows.
Still some of you might be wondering, if it’s for older systems how come so many big companies also kena. Well that’s the thing la, it seems that many companies are still using older versions of Windows because it’s not easy or cheap to continuously upgrade your system.
“Many NHS trusts still use Windows XP, a version of Microsoft’s operating system that has not received publicly available security updates for half a decade, and even those which are running on newer operating systems are often sporadically maintained.” – Columnists Alex Hern and Samuel Gibbs, as quoted by The Guardian
But perhaps we also do need to mention that there was a bit of news going around about how e-banking and online retail could also lead to you getting the WannaCry virus, but so far there has been no proof of that happening, and the gomen themselves has said it’s not true.
Anyway, in the event that your computer is infected, you will notice that your computer will look something like this.
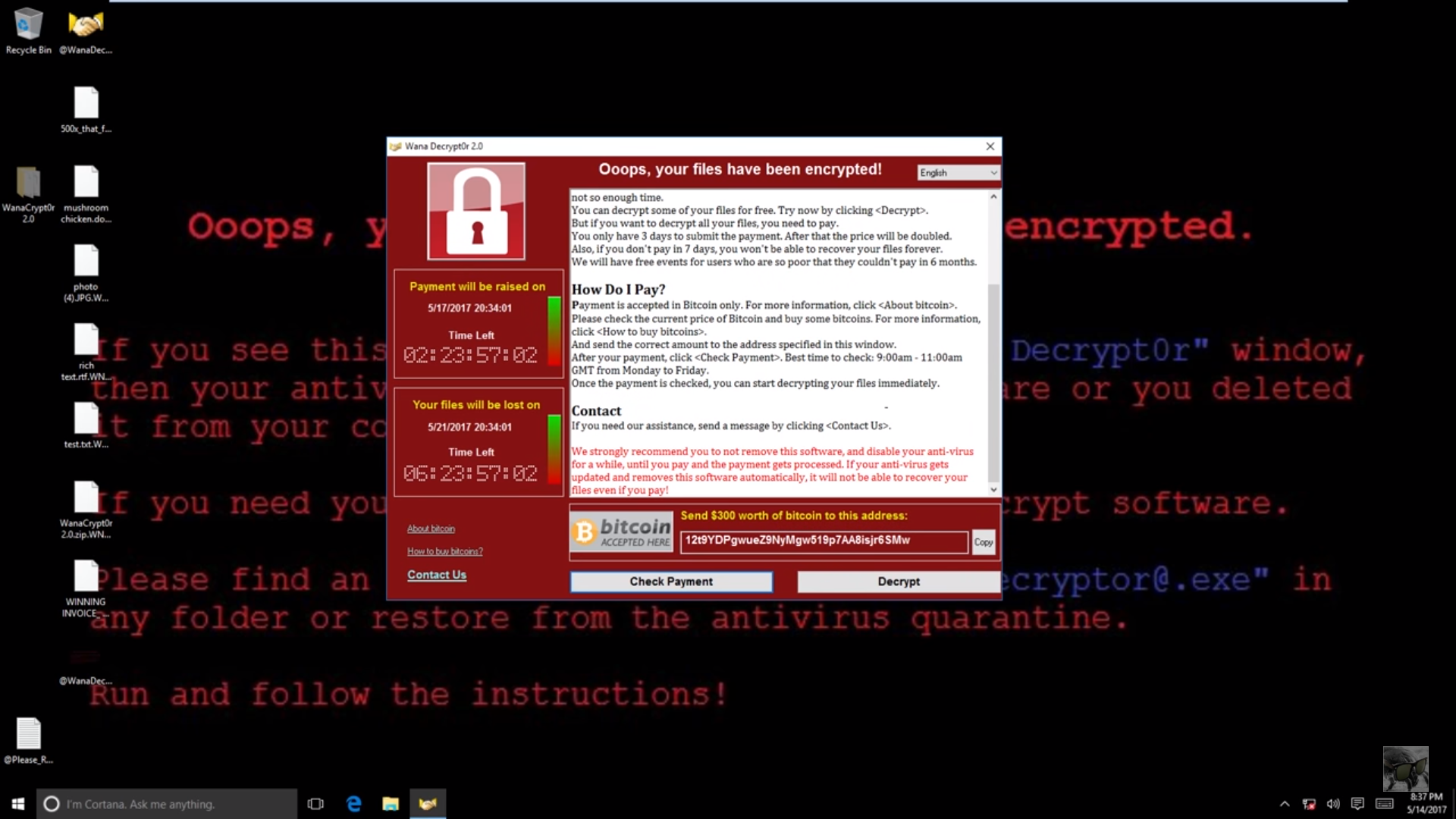
The first thing to take note is that the screen says your files have been encrypted.
“Fundamentally, encryption is the act of scrambling communication to stop people other than its intended recipient from reading it.” – Columnist James Titcomb, on Telegraph UK
Our Whatsapp messages are also (supposedly) encrypted, and these are actually meant to protect us, but in this case, ransomware uses it to give us problems instead.
The next thing is that the screen shows you 2 timers:
- One showing you the time remaining before it raises the ransom amount.
- The other showing you the time remaining before your files are deleted.
If the first timer expires, it doubles your ransom from US$300 (RM1,300) to US$ 600 (RM2,600). As for the second timer, well no explanation needed la. And they would only receive the money in bitcoin format, which is a form of online currency but that is a whole other topic on its own so if you wanna know more you can read about it here.
But what do I do if my computer is infected?

1. Pay the ransom
Do consider that even though that there have been reports that the WannaCry software has already generated US$50k in ransom money, there are several reasons why it’s not advisable for you to pay like there’s no guarantee that your files will be returned to you after you pay, and it actually may encourage them to do more dastardly things like this.
BUT these articles also mention that this really depends on how important the files in your computer are. Is it worth risking for and paying RM1000+ for it? If it is then you make the call and hope for the best.
2. Restore your computer to a previous version
What this means is that your computer kinda travels back in time and restores itself to how it was at a particular time. *Spoiler alert!* Kinda like how Superman turned back time to bring Lois Lane back to life, or when Dr Strange reverses time to undo the damage done by the bad guy.
But the problem with this method is that your computer must already have a restore point. Certain Windows systems would already be backing up your data and creating restore points but the problem is some computers may not, and even if you do it, it doesn’t mean it will undo the encryption on the files.
3. Use other software to remove WannaCry
Alternatively, there have been people out there claiming that they have the software to remove WannaCry. But it isn’t free though, and may be very risky on it’s own.
And if all else fails, you may have only one option left:
4. Reformat your computer
It will completely reset your computer to how it looked when you first bought it, meaning you will lose all your files BUT it ensures that WannaCry (and any other virus for that matter) is completely removed. You can either just bring your computer to your local computer shop and ask them to do it for you, or read about how to do it yourself here.
And even if your computer is fully updated and protected, please, please, still try to be as safe as possible when using the internet because…
The WannaCry ransomware is still “evolving”

Even if it did affect computers in 150 countries, WannaCry’s spread was actually reduced when a tech guy discovered a “kill switch” by accident. The creators of WannaCry had created like some sort of command to stop WannaCry completely if they wanted to (possibly to kill it if it ever got out of control), and this guy happened to stumble upon it, and slowed WannaCry’s spread.
But this doesn’t seem to be the end of similar ransomware because there have been multiple reports that variants of the WannaCry virus have emerged – ransomware that ain’t got no kill switch. And despite the Windows patch, some are still saying that it doesn’t mean that the threat is over.
“It’s probably going to get worse before it gets better, as it’s going to be one of the most serious threats for the following 12 months.” – Catalin Cosoi, Bitdefender’s chief security strategist, as quoted by PCWorld
In fact, our gomen is taking this so seriously that the National Security Council (NSC) is now overseeing our fight against it. CyberSecurity Malaysia (also under the gomen) asks that if you are infected, please let them know so that they can help you. And for the time being, their advice is this:
“System administrators are urged to patch their systems and keep their users aware of the new ransomware in order to prevent them from clicking on suspicious emails or files. – Datuk Amirudin Abdul Wahab, CEO of CyberSecurity Malaysia, as quoted by The Malay Mail Online
And perhaps if we all work together, we’ll be able to keep the monster that is WannaCry at bay.
- 2.1KShares
- Facebook2.0K
- Twitter7
- LinkedIn14
- Email20
- WhatsApp37