The US is spying on other countries by selling them this machine. Malaysia bought one.

- 639Shares
- Facebook584
- Twitter2
- LinkedIn9
- Email8
- WhatsApp36
While spy stuff are commonly seen in movies like James Bond and Mission Impossible, we all know that it’s very much a real thing. And in a lot of instances, spies communicate with code that only they would understand. So the way it basically works is that you would need a code-making machine and a code-decrypting machine for smooth communication between spies.
But you see, things are only secure if only spies within country has access to the codes, and not so much when another country has access to the codes as well, which is kind of what happened when Malaysia bought encryption devices from the US’ Central Intelligence Agency (CIA).

Earlier this month, The Washington Post published an investigative report with details of how the CIA used to sell rigged devices to Malaysia, among others, to spy on us. It was apparently called:
“…the intelligence coup of the century.” – The Washington Post
Before you continue reading, keep in mind that many things in this article have not actually been confirmed, so do mentally add in “allegedly” as you read.
And now you’re probably thinking: how did the CIA spy on us?
They bought and owned the company selling the devices
…and this company was called Crypto AG.

Crypto AG was a Swiss company that sold encryption devices across the world, founded in as early as the 1940s. The company got its big break when it began to sell encryption machines to American soldiers in World War II, and soon soared to become the top supplier of such devices to over 120 countries, including Iran, Latin American nations, India, Pakistan, and, yes, Malaysia.
Apparently, the devices were so well made that even after the war, the US came to an agreement with the company, basically demanding it to only sell its products to US-approved countries in the 1950s. It was a deal that pretty much sold its ownership to the CIA. The Washington Post called it a “denial operation“.
“[Crypto AG] could sell any machine to any NATO countries, plus Switzerland and Sweden. As for the rest, the agreement had an attached chart showing who could buy what.” – Leaked CIA document, as quoted by The Washington Post

And this deal was so successful that, apparently, the encryption devices gave the US an edge to win the Cold War. But it was only in the 1970s that the CIA began actively upgrading the devices. And it was at this time when other countries began clamoring for these supposedly superior devices by the CIA, and that’s including Malaysia.
Presumably, these devices allow the CIA to listen in on, collect, and decode data used and sent by Malaysia, even though they’re promised to be top notch encryption devices. Imagine if you bought a set of lock and keys from the locksmith, but he also made himself a same set of keys – that’s kind of how it worked with the CIA devices.
“Imagine the idea of the American government convincing a foreign manufacturer to jimmy equipment in its favor. Talk about a brave new world.” – Leaked CIA document, as quoted by The Washington Post
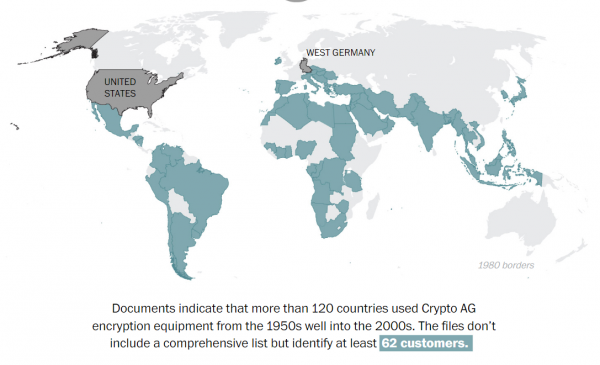
It’s unclear as to when Malaysia began to purchase these devices, but we’re listed as one of Crypto AG’s clients in The Washington Post, so it’s possible that the codes we’ve been sending using these encryption devices have been decoded by the US.
“The United States and its allies exploited other nations’ gullibility for years, taking their money and stealing their secrets.” – Leaked CIA document, as quoted by The Washington Post

The CIA made a boatload of a cash from the sales, generating millions of dollars in profits for the agency, allowing Crypto AG to even once establish an office in Malaysia. It’s even believed that Crypto AG’s devices make up about “40% of the diplomatic cables and other transmissions by foreign governments“, providing just as much data for the US to decode and gather intelligence.
However, the company was eventually dissolved and absorbed by a company called Crypto International in 2018, which has denied any further involvement with any national security organization, and the Crypto AG office in Malaysia is also gone now.
But still, knowing that the CIA had always had some sort of a backdoor to our system is kind of scary, because who knows what kind of information the US could have siphoned off from us through the rigged devices? So now you probably think it’s the end of the article, but – dun dun dun – the CIA might not be the only one who’s been spying on us, because…
The US’ trade war rival, China, could be spying on us too (◯Δ◯∥)

Almost around the same time as when the CIA report surfaced, the Malaysia Computer Emergency Response Team (MyCERT) issued a warning that our government officials are potentially targeted by a China-linked group, APT40. MyCERT is a team set up by the government, meant to offer references for Malaysians to deal with cyber security problems, so they’re may have a point.
APT40 is allegedly a group of hackers who are apparently funded by the Chinese government, and it’s been active since 2013. It also allegedly targets industries related to engineering, transportation, and defense, especially when these industries overlap with maritime technology – a fancy word for anything related to the sea.
But APT40 is only one among many APT groups attributed to China, which are also known as Advanced Persistent Threat Groups. There are allegedly 10 more APT groups attributed to China, all based in different Chinese provinces and targeting different countries, with APT40 targeting Malaysia.

A lot of APT40’s projects have also been found to be aligned with the interests of the Chinese government. Some have even claimed that APT40 consists of contractors who operate under the supervision of the Hainan Division of State Security Ministry in China.
“APT groups in China have a common blueprint: contract hackers and specialists, front companies, and an intelligence officer. We know that multiple areas of China each have their own APT.” – Cybersecurity group Intrusion Truth, as quoted by ZDNet
What it usually does is try to steal data, destroy operations, or destroy infrastructure.
APT40 seems to mainly targets countries important to the Belt and Road Initiative
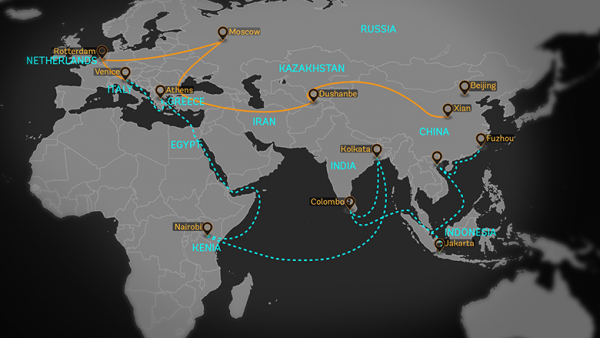
The Belt and Road Initiative (BRI), also known as the New Silk Road, is an infrastructure project launched by China’s president Xi Jinping in 2013. It’s a trade network involving railways, energy pipelines, highways, and border crossings throughout former Soviet countries, Pakistan, India, and Southeast Asia.
This project has been pretty controversial in the past few years, because there are some who are afraid that the BRI will be an “unsettling extension of China’s power“. Just last year, Malaysia’s also been embroiled in a BRI controversy of its own with a comic book that is supposedly a propaganda comic in BRI’s favor.
And APT40’s been found to be targeting Southeast Asian countries that are involved in the initiative. Coincidentally, these countries are also major actors in the South China Sea dispute.
Its methods of spying are:
- Pose as journalists, someone from a trade publication, or an individual from a relevant military organization or NGO
- Establish contact with government officials
- Steal information by sending phishing emails

Phishing emails are fraudulent emails that are made to resemble they’re from a company you know or trust – a bank, credit company, or online payment website etc. – and their end goal is to steal sensitive information from the targets.
There’ll be files or links to documents stored on Google Drive attached in the APT40 emails, all of which will contain a string of malicious codes to install malware in the targets’ devices once opened. The malware allows APT40 to pass through password-protected barriers and log on to systems that the targets are connected to.
“The group’s operations tend to target government-sponsored projects and take large amounts of information specific to such projects, including proposals, meetings, financial data, shipping information, plans and drawings, and raw data.” – MyCERT
APT40’s alleged goal in doing this is to steal data and infiltrate our systems, specifically collecting information on major projects related to BRI, which Malaysia is very much a part of. The details of the coding used in their phishing emails can be found here, which you can look through if you’re somewhat of an expert.
If APT40 had been successful and it truly is working for the Chinese government, then it is likely that China might have been spying on the BRI progress in Malaysia, maybe even things that the rakyat don’t know about.
But…
Malaysia does have cyber security measurements in place

Soon after The Washington Post report was published, our Home Affairs Minister Muhyiddin Yassin reassured us that the rigged devices that bought from Crypto AG were not used to transfer sensitive information, further adding that our government has taken cautious steps to prevent information from being leaked.
In addition, our Inspector-General of Police Abdul Hamid Bador also said that the devices were only used for “short-term communication operations” and had nothing to do with hyper sensitive matters.
“Malaysia is not the only country which uses the technology. I have discussed this matter with the Inspector-General of Police, and we assure that the technology is not used to disseminate any form of confidential data.” – Muhyiddin, as quoted by NST
Plus, MyCERT couldn’t confirm whether the APT40 had been successful in stealing information from our government officials, though it did manage to trace a cyber-attack campaign against our government officials by the group.
Regardless, Malaysia has several cyber security agencies, public and private, to combat cyber-attacks, such as CyberSecurity Malaysia, National Cyber Security Agency (NACSA), and MyCERT. In addition, our Deputy Prime Minister Wan Azizah Wan Ismail has also said that the government is developing a master plan on cyber security to implement cyber security awareness programs throughout the country.
“This initiative will help the government to identify weaknesses and gaps in terms of procedures and technical expertise of the critical agencies towards improving cyber security in the country.” – Wan Azizah, as quoted by Malaymail
All things considered, it’s been said that our government is pretty well-equipped in combating cyber-attacks. So unless something really serious happens in the future, the best we can do is trust that our government will try their best to avoid foreign attacks, online or offline.
Although governments are working hard to avoid getting attacked, we can be easy targets too. We can however avoid becoming a victim of cybercrime much easier with NORDVP – just kidding. What you can actually do is to avoid logging in to your important accounts on insecure networks and installing a dependable anti-virus program. Remember – always use protection.
- 639Shares
- Facebook584
- Twitter2
- LinkedIn9
- Email8
- WhatsApp36




