SayaKenaHack.com checks if you have been hacked. But where did THEY get the info?[Update]
- 1.2KShares
- Facebook1.1K
- Twitter9
- LinkedIn23
- Email15
- WhatsApp58
[Update 20/11/17: A fake “official” data leak checking website has popped up over the weekend, because the creator wanted to teach people a lesson about trusting websites that asks for you personal info. You can read about it here.]
[Update 17/11/17: Keith will be taking down the website at midnight of Sunday. You can read his full explanation here.]
[UPDATE: Just as we were going to launch this article, MCMC has blocked SayaKenaHack.com. The block doesn’t seem to be complete as some of us can still access it. Meanwhile, you can refer to this article to unblock it if you’re blocked.]
You may have heard about the recent data breach in Malaysia, or maybe even read our article about the issue. Recently, CIMB reported that some of its tapes containing back up customer data were physically lost during a routine operation. They added that while some of the tapes contained customer information, no authentication data such as pin numbers, passwords and credit card numbers were in there.
“Following a thorough and ongoing assessment, there is currently no evidence that any of this information has been compromised.” – CIMB, quoted from MalaysiaKini
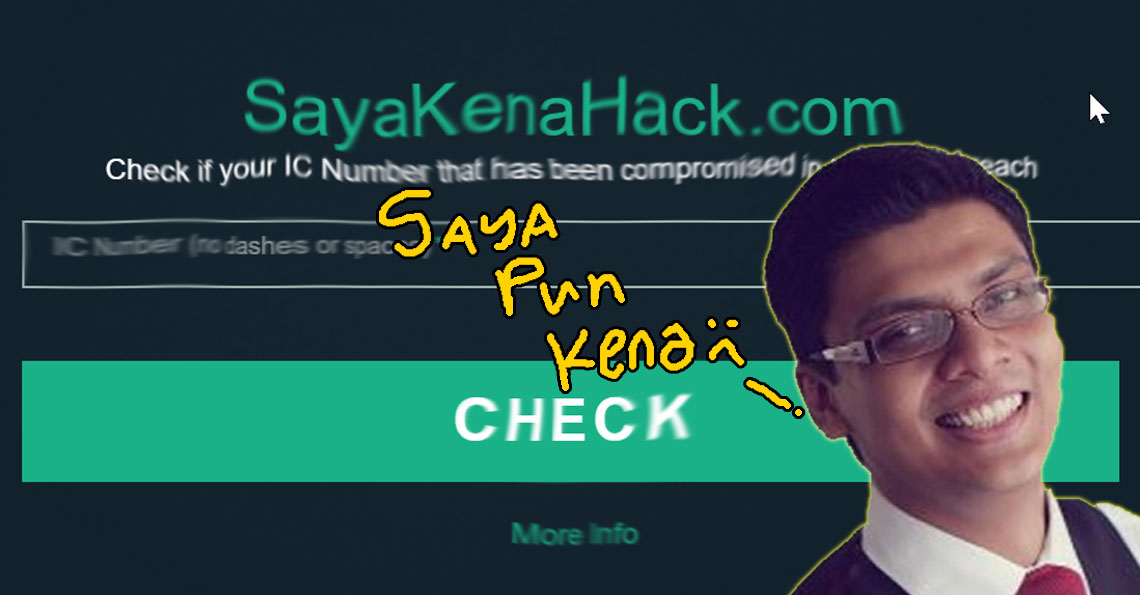
In the meantime, we stumbled upon something quite interesting. Someone had made a website called SayaKenaHack.com, for people like you and me to find out if our information was leaked in the breach.
Of course, it’s only natural to be skeptical when a totally unknown website asks you for your IC number, especially with all that’s been happening. What if this was a scam to scam those who worry they might get scammed? Because people have been using this data to scam Malaysians. So, we got in touch with the creator to find out if you will kena hack or not when you use this website.
Actually, the breached data is available for free… if you know where to find it
Meet Keith, an avid Malaysian tech blogger and self proclaimed The Insufferable Tech Evangelist and creator of SayaKenaHack.com. By day he’s an Application Architect for a large corporation, other times, he hacks 4 UniFi accounts under 5 minutes. We’ve interviewed him a couple of times for tech and/or hacking stuff.

Keith’s website basically matches the IC number you put in to its database. In other words, it already knows all the breached IC numbers and hand phone numbers, whether we want to use it or not. By extension, it also means Keith has all the data we’re afraid of revealing. If you’ve already forgotten what those data includes, you can recap here. So the question is, how did Keith get all that information?!
“The data was available on a dark market forum for some time, before being posted on a separate hacker forum (that is on the clear web). Those ‘hackers’ on Lowyat were merely re-sellers. No hacker would open up a file on a windows machine.” – Keith told CILISOS
Keith spent 40+ hours and an undisclosed amount of cookies and cupcakes to build the website. There’s some special technical stuff that he’s proud of applying, but meh, ugaiz wouldn’t wanna know that. Worse than that, Keith tells us that the data continues to be available on a hacker forum, for FREE. So Keith did not pay anything for the data, or in his own words:
“I would never validate the business case of reselling stolen data.” – Keith wrote on his blog
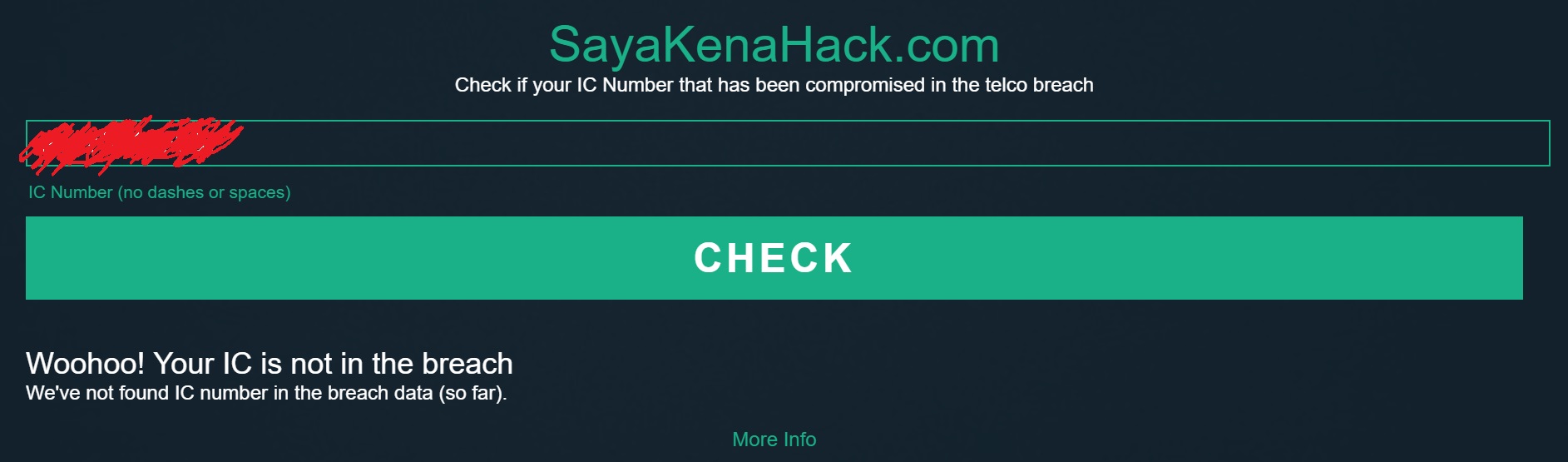
In fact, Keith himself also kena! You can also rest a little more easy because Keith says that all the data is masked. For example, only the first 4 and last 2 digits of the phone number is available. Once we felt a little braver after knowing how it works, we tried to key in our IC numbers. You will either get a result like this if you’re clear,
Or this result if your information was in the breached data.
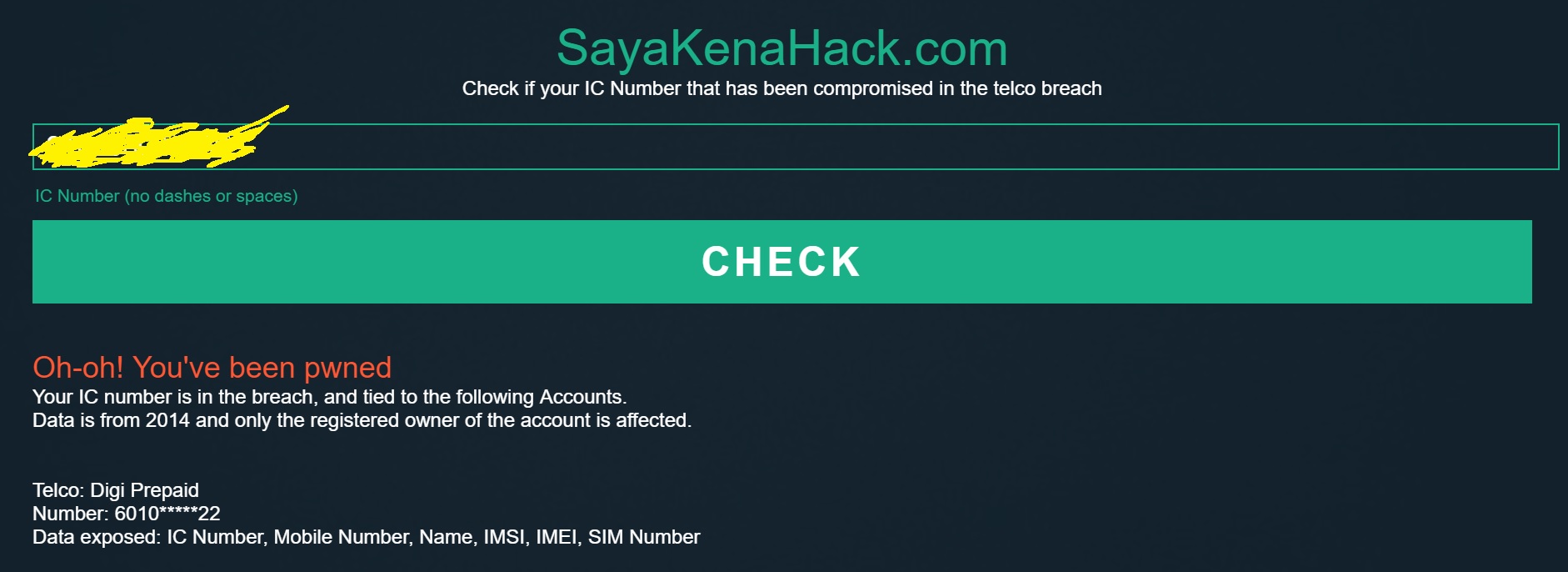
As a reminder, the data here is only from 2014, so if your phone is newer there will be less to worry about. When we launched this article, about 100,000 people already visited the website. For now, Keith has only uploaded data from Maxis, Digi, Celcom and UMobile, and plans to add the smaller telcos when he has the time. As for the other sources, he is still unsure whether he should make it available.
Who hacked who and WHY!?

Considering that the ones that posted on Lowyat were re-sellers, that would mean there has to be a original hacker/ source for the data. Additionally, if the data is widely available now on hacker forums and such, does that mean that the data was successfully sold? We asked Keith if he knew anything more about where the data might have come from.
“In hacker terms this was probably done “for the lulz”. It was freely available before the Lowyat incidence,” – Keith
For those not familiar with internet slangs, “for the lulz” simply means for the fun of it. So to put it simply, because the data has been freely available to those who knew where to look for it, someone might have hacked and released the data just for the fun of it. This sporting spirit is not strange considering that Keith himself made SayaKenaHack.com despite knowing that there’s nothing much we can really do even if you found out that your data has been breached.
But, we still asked him why he did it anyway:
“Just because you can’t do anything about it doesn’t mean people don’t have the right to know. I’m not pretending it has a deeper fundamental meaning, it’s just a side hobby of mine—but at its core the site is about informing the public and hopefully kickstart a larger conversations about this. But if people don’t care, that’s fine. But people need to be aware.” – Keith
Oh and which hacker so rajin to hack ALL the telcos!?

We also wondered if he might know where the hackers could have gotten the source from. As we said before, almost all major and minor telco companies were involved in the breach.
Like… have you even HEARD of Friendi, XOX, PLDT and… EnablingAsia!? Wow… we sure haven’t. Yep, they’re all telcos that have had their data compromised.
According to Keith, there are 2 possibilities how the hacker(s) might have gotten the info:
- Someone hacked every telco company individually to get the data
- Someone hacked a central source that keeps data from all the telco companies
But one has to wonder the likeliness of possibility 1, especially when you look at the full list of companies that were breached. Possibility 2 just becomes more plausible, and it’s around this time when these sentences in Keith’s blog caught our attention:
“Consider also, that if you downloaded the data, (which I obviously have), it’s clear as day where the leak came from. It’s so clear, Stevie Wonder can see where the data was leaked from.” – keithRozario.com
The following is entering conspiracy theory area, but bear with us. If the 2nd possibility is true, who in Malaysia would possibly have the data from all telco companies that operate here? When we pressed Keith for more information on this, he sadly declined to comment. A data analysis company that all telcos happen to work with?? Or someone else that the companies are required to give information to???
ON A TOTALLY UNRELATED TOPIC, we probably shouldn’t speculate too much, since the MCMC asked us not to (and we just got a letter from them last week for our Halloween article).
“MCMC is working closely with police and it is crucial at this juncture to refrain from making any speculation or conclusion as it can affect the ongoing probe.” – MCMC Chief Operating Officer Dr Mazlan Ismail, quoted from New Straits Times
Oh and as reflected in our update, they closed down Keith’s site too (!).
When we catch whoever’s responsible, who should be held accountable?
According to the Personal Data Protection Act 2010, whoever is in possession of people’s personal information without license will be the first ones to get in trouble (sadly, that can also include Keith). But at the same time, companies, or whoever is collecting and storing these personal data in the first place, has the responsibility to protect and ensure safe-keeping of that information. Failure of that is worth a fine of RM300,000 or imprisonment for no more than 2 years or both.

Even in past security breaches overseas, its still quite debatable how much responsibility companies should hold in the event of a data breach. In the case of Sony’s PlayStation 2011 breach, Sony has both been successfully charged in UK when the authorities deemed the breach “could have been prevented”.
“If you are responsible for so many payment card details and log-in details then keeping that personal data secure has to be your priority. In this case that just didn’t happen, and when the database was targeted – albeit in a determined criminal attack – the security measures in place were simply not good enough.” – ICO deputy commissioner David Smith, quoted from The Verge
But there was a different outcome in U.S. California, where the judge deemed that Sony couldn’t have been fully responsible for it and dismissed the case.
“There is no such thing as perfect security.” – Judge Anthony Battaglia, quoted from CNET
Since then, Sony has changed its terms and conditions for using the PlayStation Network to allegedly minimise its lossses. They’ve included a term for users to try and resolve legal issues with an arbitrator picked by Sony before being able to file a lawsuit against them.
While companies are responsible for the keeping the information safe, there’s a line on how much they can do, and that’s drawn in the courts. Even the N.S.A, the super secret spy base in U.S is vulnerable to hacks and data leaks!
“No one can build an unhackable system, both technically and operational that is impossible.” – Keith

THIS MIGHT BE THE BIGGEST DATA BREACH IN MALAYSIAN HISTORY, AND ALL MALAYSIANS ARE AT RISK
HERE’S HOW OUR GOMEN CAN BLOCK WEBSITES IN MALAYSIA
MAS HACKED? 5 MORE MALAYSIAN HACKING CASES YOU MAY HAVE FORGOTTEN
- 1.2KShares
- Facebook1.1K
- Twitter9
- LinkedIn23
- Email15
- WhatsApp58



